 Mnemonic code
Mnemonic code
for generating deterministic keysMnemonic:
bip39 0.2 | 2305
... ...
... ... ...
Bitcoin Improvement Proposal 39, or BIP39, is a protocol that was introduced as a means to generate deterministic wallets.
It's a method for creating a human-readable mnemonic words – easy to read and write – from random data that serves
as a backup to recover your wallet. It is an open-source protocol that is widely adopted in the cryptocurrency industry including Trezor.
SLIP039 - standard implementation of Shamir's secret-sharing (SSS) for backing up Hierarchical Deterministic Wallets (BIP-0032). SSS divides a master secret into parts, with a minimum number needed to reconstruct it. Fewer parts reveal no information about the secret. This SLIP is designed as a replacement for BIP-0039 and is largely incompatible with it.
SLIP039 - standard implementation of Shamir's secret-sharing (SSS) for backing up Hierarchical Deterministic Wallets (BIP-0032). SSS divides a master secret into parts, with a minimum number needed to reconstruct it. Fewer parts reveal no information about the secret. This SLIP is designed as a replacement for BIP-0039 and is largely incompatible with it.
In the world of cryptography and digital assets, one of the most critical aspects of managing digital assets
is the ability to restore them in case of device loss or failure. BIP39 provides an excellent solution for this issue,
as it presents a more user-friendly method of backup compared to random strings of characters.
(Trezor)
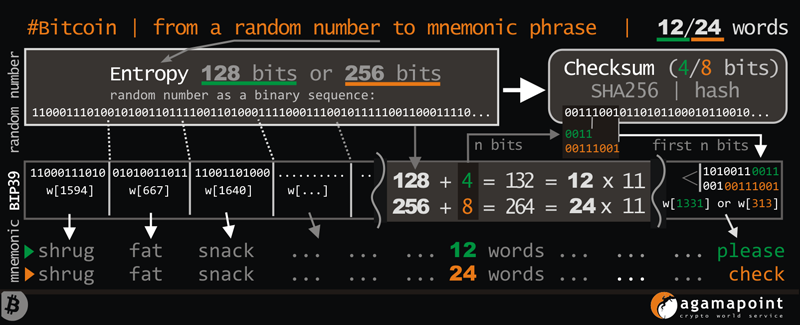
Entropy: The input hexadecimal string (entropy)
must be of a length that is a multiple of 32 bits. Examples of entropy lengths are 128, 160, 192, 224, or 256 bits.
SHA-256: A SHA-256 hash is computed from this entropy.
Checksum: The first bits of this SHA-256 hash are taken. The number of checksum bits is equal to the length of the entropy in bits divided by 32. For example, if the entropy length is 128 bits, the checksum has 4 bits; if the entropy length is 256 bits, the checksum has 8 bits.
SHA-256: A SHA-256 hash is computed from this entropy.
Checksum: The first bits of this SHA-256 hash are taken. The number of checksum bits is equal to the length of the entropy in bits divided by 32. For example, if the entropy length is 128 bits, the checksum has 4 bits; if the entropy length is 256 bits, the checksum has 8 bits.
Extended Entropy: The checksum is appended to the binary string of the entropy. The resulting binary string is
then divided into groups of 10/11 bits.
Dictionary: Each 11-bit block is converted into a decimal number, which serves as an index for selecting words from the BIP39 dictionary.
With 11 bits, we can have 211 or 2048 unique values, which corresponds to a dictionary of 2048 words.
Dictionary: Each 11-bit block is converted into a decimal number, which serves as an index for selecting words from the BIP39 dictionary.
With 11 bits, we can have 211 or 2048 unique values, which corresponds to a dictionary of 2048 words.
TEST Automatic insert:
| I: 0011 | A: 0111 | T: 0011 |
| I: 0011 | A: 0111 | T: 0011 |
NEVER download data from this site for real use, the data generated here is only for clarification of the principle.
If you share the information generated by this page with anyone, they can steal your assets. Anyone asking you to share your your secret recovery phrase or BIP 32 root key is a scammer. Do NOT copy & paste information from this page or send it to anyone offering to help you on Twitter, Discord, Telegram, Etherscan, or Line. They will steal your coins!
If you share the information generated by this page with anyone, they can steal your assets. Anyone asking you to share your your secret recovery phrase or BIP 32 root key is a scammer. Do NOT copy & paste information from this page or send it to anyone offering to help you on Twitter, Discord, Telegram, Etherscan, or Line. They will steal your coins!
SLIP-00039 |
github.com/trezor/python-shamir-mnemonic |
agama_point_crypto/../ slip2_ 3generate_vectors.py | slip3_5recovery.py
agama_point_crypto/../ slip2_ 3generate_vectors.py | slip3_5recovery.py
:.: Security | Padded share value length | Total share length ----------+---------------------------+------------------- 128 bits | 130 bits 200 bits = 20 words 256 bits | 260 bits 330 bits = 33 words 20 words: 2 - 2 - 13 - 3 The first two words are random but the same for all multishare backup sets. The third and fourth words contain information about the number of sets and the number required to recover the wallet. The following 13 words (i.e., words 5 to 17) represent the actual seed. The last three words (i.e., words 18 to 20) form the checksum.
Format of the share mnemonic • identifier (id) field is a random 15-bit value that is the same for all shares and verifies that they belong together. • extendable backup flag (ext) field indicates whether the id is used as salt in the encryption of the master secret (ext = 0). • iteration exponent (e) field specifies the number of iterations in PBKDF2, calculated as 10000×2^e. • group index (GI) field represents the x value of the group share. • group threshold (Gt) field indicates the number of group shares needed to reconstruct the master secret, encoded as Gt = GT − 1. • group count (g) indicates the total number of groups, encoded as g = G − 1. • member index (I) field is the x value of the member share in the group. • member threshold (t) field shows how many member shares are needed to reconstruct the group share, encoded as t = T − 1. • padded share value (ps) field is a list of the SSS part's fk(x) values, each encoded as an 8-bit string. The share value is left-padded with "0" bits to make its length a multiple of 10. • checksum (C) field is an RS1024 checksum of the share's data part. The RS1024 customization string is "shamir" for ext = 0 and "shamir_extendable" for ext = 1. bits id ext e GI Gt g I t ps C 15 - 1 - 4 --- 4 - 4 - 4 - 4 - 4 --- +8 ---- 30 2 - 2 - 13 - 3 12 * 11 = 132 13 * 10 = 130 12 * 10 + 8 = 128
SLIP-0039: - standard and interoperable implementation of Shamir's secret-sharing (SSS) and a specification for its use in backing up Hierarchical Deterministic Wallets described in BIP-0032. SSS splits a master secret into unique parts which can be distributed among participants. A specified minimum number of parts is required to be supplied in order to reconstruct the original secret. Knowledge of fewer than the required number of parts does not leak information about the master secret. This SLIP is mainly intended as a replacement for BIP-0039 and for the most part, the two are not compatible.
id ext e GI Gt g I t ps C
15 - 1 - 4 --- 4 - 4 - 4 - 4 - 4 --- +8 ---- 30
2 - 2 - 13 - 3
3/2: album academic acrobat leader curly endless ...
1/1: purple branch academic academic antenna ...
9/5: walnut flea agree academic acne skin rapids ...
walnut 10 | zero 11
:.